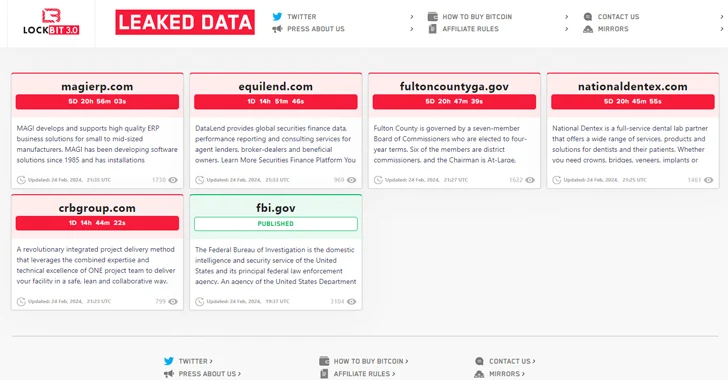
The threat actors behind the LockBit ransomware operation have resurfaced on the dark web using new infrastructure, days after an international law enforcement exercise seized control of its servers. To that end, the notorious group has moved its data leak portal to a new .onion address on the TOR network, listing 12 new victims as of writing. The administrator behind LockBit, in a lengthy follow-up message, said some of their websites were confiscated by most likely exploiting a critical PHP flaw tracked as CVE-2023-3824, acknowledging that they didn’t update PHP due to “personal negligence and irresponsibility.” “I realize that it may not have been this CVE, but something else like 0-day for PHP, but I can’t be 100% sure, because the version installed on my servers was already known to have a known vulnerability, so this is most likely how the victims’ admin and chat panel servers and the blog server were accessed,” they noted. They also claimed the U.S. Federal Bureau of Investigation (FBI) “hacked” their infrastructure because of a ransomware attack on Fulton County in January and the “stolen documents contain a lot of interesting things and Donald Trump’s court cases that could affect the upcoming U.S. election.” In addition to calling for attacking the “.gov sector” more often, they stated that the server from which the authorities obtained more than 1,000 decryption keys held almost 20,000 decryptors, most of which were protected and accounted for about half of the total number of decryptors generated since 2019. The group further went on to add that the names of the 194 affiliates have “nothing to do with their real nicknames on forums and even nicknames in messengers.” That’s not all. The post also attempted to discredit law enforcement agencies, claiming the real “Bassterlord” has not been identified, and that the FBI actions are “aimed at destroying the reputation of my affiliate program.” “Why did it take 4 days to recover? Because I had to edit the source code for the latest version of PHP, as there was incompatibility,” they said. “I will stop being lazy and make it so that absolutely every build loker will be with maximum protection, now there will be no automatic trial decrypt, all trial decrypts and the issuance of decryptors will be made only in manual mode. Thus in the possible next attack, the FBI will not be able to get a single decryptor for free.” Russia Arrests Three SugarLocker Members The development comes as Russian law enforcement officials have arrested three individuals, including Aleksandr Nenadkevichite Ermakov (aka blade_runner, GustaveDore, or JimJones), in connection with the SugarLocker ransomware group. “The attackers worked under the guise of a legitimate IT firm Shtazi-IT, which offers services for the development of landing pages, mobile applications, scripts, parsers, and online stores,” Russian cybersecurity firm F.A.C.C.T. said. “The company openly posted ads for hiring new employees.” The operators have also been accused of developing custom malware, creating phishing sites for online stores, and driving user traffic to fraudulent schemes popular in Russia and the Commonwealth of Independent States (CIS) nations. SugarLocker first appeared in early 2021 and later began to be offered under the ransomware-as-a-service (RaaS) model, leasing its malware to other partners under an affiliate program to breach targets and deploy the ransomware payload. Nearly three-fourths of the ransom proceeds go to the affiliates, a figure that jumps to 90% if the payment exceeds $5 million. The cybercrime gang’s links to Shtazi-IT were previously disclosed by Intel 471 last month. The arrest of Ermakov is notable, as it comes in the wake of Australia, the U.K., and the U.S. imposing financial sanctions against him for his alleged role in the 2022 ransomware attack against health insurance provider Medibank. The ransomware attack, which took place in late October 2022 and attributed to the now-defunct REvil ransomware crew, led to the unauthorized access of approximately 9.7 million of its current and former customers. The stolen information included names, dates of birth, Medicare numbers, and sensitive medical information, including records on mental health, sexual health, and drug use. Some of these records also found their way to the dark web. It also follows a report from news agency TASS, which revealed that a 49-year-old Russian national is set to face trial on charges of carrying out a cyber attack on technological control systems that left 38 settlements of the Vologda region without power. Update LockBit has removed EquiLend and Ernest Healthcare from its data leak site as of February 29, 2024, raising the possibility that the cybercrime group may be attempting to protect its standing within the cybercrime community. “We are 99% sure the rest of their ‘new victims’ are also fake claims (old data for new breaches),” security firm RedSense said in a post shared on the social media platform X. “So the best thing for them to do would be to delete all other entries from their blog and stop defrauding honest people.” LockBit Saga — Timeline of Events February 20, 2024 LockBit Busted – Authorities Seize Darknet Domains An international law enforcement operation, including 11 countries and Europol, successfully seized darknet domains linked to the ransomware group LockBit, which has extorted over $91 million since 2019. The operation, named Cronos, used a PHP security flaw to disrupt LockBit’s websites, marking a significant blow to the group’s activities. February 21, 2024 LockBit Hackers Arrested – Decryption Tool Released UK’s NCA shuts down LockBit ransomware, arrests 2 in Poland/Ukraine, freezes 200+ crypto accounts, indicts 2 Russians in US. Seized LockBit’s code, intelligence, dismantled 34 servers, retrieved 1k decryption keys. LockBit affected 2.5k victims globally, netted $120M. Decryption tool available for victims. February 22, 2024 $15 Million Bounty on LockBit Ransomware Leaders US State Dept offers $15M reward for info on LockBit ransomware leaders, involved in 2k+ global attacks since 2020, causing $144M in damages. Law enforcement disrupted LockBit, arresting affiliates and seizing assets. LockBit, known for ransomware-as-a-service, extensive affiliate network, and innovative tactics like a bug bounty program, remains a significant cyber threat despite setbacks. February 25, 2024 LockBit Ransomware Kingpin ‘Engages’ with Police The individual(s) behind the LockBit ransomware service, known as LockBitSupp, has reportedly engaged with law enforcement following a significant international crackdown on the ransomware-as-a-service operation named Operation Cronos. February 26, 2024 LockBit is Back – Calls for Attacks on US Government The LockBit ransomware group has re-emerged on the dark web with a new infrastructure shortly after law enforcement seized its servers. The group has listed 12 new victims on its data leak portal and discussed the seizure of its websites, attributing it to a potential exploitation of a PHP vulnerability.
This content was originally published here.