A newly discovered campaign dubbed “Stayin’ Alive” has been targeting government organizations and telecommunication service providers across Asia since 2021, using a wide variety of “disposable” malware to evade detection.
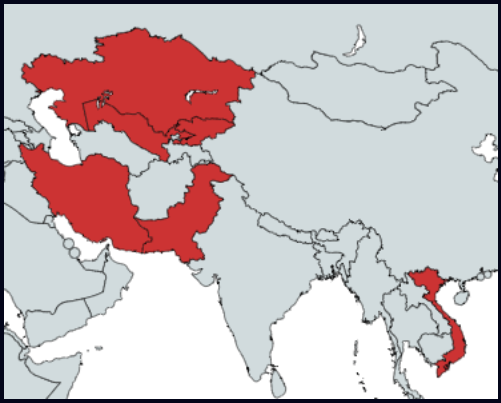
Most of the campaign’s targets seen by cybersecurity firm Check Point are based in Kazakhstan, Uzbekistan, Pakistan, and Vietnam, while the campaign is still underway.
The attacks appear to originate from the Chinese espionage actor known as ‘ToddyCat,’ which relies on spear-phishing messages carrying malicious attachments to load a variety of malware loaders and backdoors.
The researchers explain that the threat actors use many different types of custom tool, which they believe are disposable to help evade detection and prevent linking attacks to each other..
“The wide set of tools described in this report are custom-made and likely easily disposable. As a result, they show no clear code overlaps with any known toolset, not even with each other,” explains Check Point.
Attack starts with an email
The attack begins with a spear-phishing email crafted to target specific individuals in key organizations, urging them to open the attached ZIP file.
The archive contains a digitally signed executable named to match the email context and a malicious DLL that exploits a vulnerability (CVE-2022-23748) in Audinate’s Dante Discovery software to side-load the “CurKeep” malware on the system.
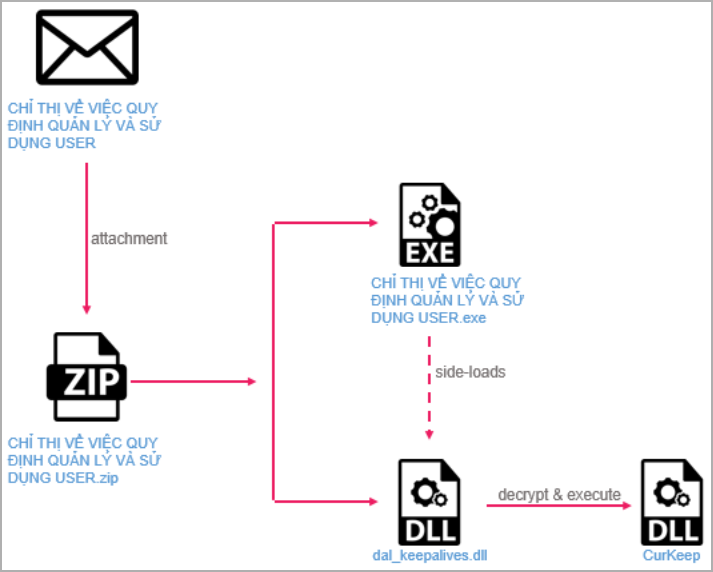
CurKeep is a 10kb backdoor that establishes persistence on the breached device, sends system info to the command-and-control (C2) server, and then waits for commands.
The backdoor can exfiltrate a directory list for the victim’s Program Files, indicating what software is installed on the computer, execute commands and send the output to the C2 server, and handle file-based tasks as instructed by its operators.
Beyond CurKeep, the campaign utilizes other tools, mainly loaders, executed primarily through similar DLL side-loading methods.
Notable ones include the CurLu loader, CurCore, and CurLog loader, each with unique functionalities and infection mechanisms.
CurCore is the most interesting of the secondary payloads, as it can create files and populate their contents with arbitrary data, execute remote commands, or read a file and return its data in base64 encoded form.
Another notable backdoor that stands out from the rest is ‘StylerServ,’ which acts as a passive listener that monitors traffic on five ports (60810 through 60814) for a specific XOR-encrypted configuration file (‘stylers.bin’).
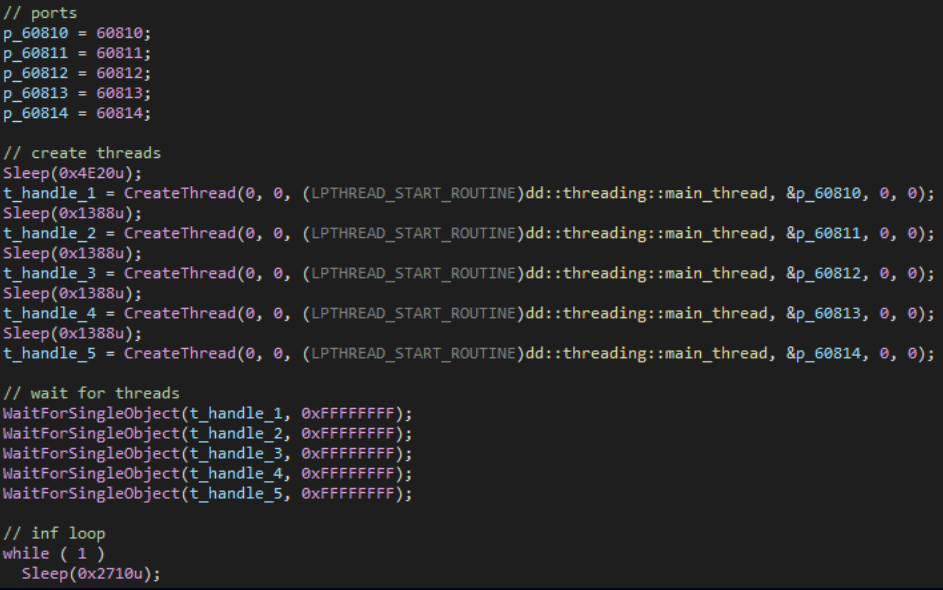
The report does not specify the exact functionality or purpose of StylerServ or stylers.bin, but it is likely part of a stealthy configuration serving mechanism for other malware components.
Check Point reports that “Stayin’ Alive” uses various samples and variants of these loaders and payloads, often tailored to specific regional targets (language, filenames, themes).
The security company says the newly identified cluster is likely a segment of a broader campaign involving more undiscovered tools and attack methods.
Judging from the wide variety of distinct tools seen in the attacks and their level of customization, these appear to be disposable.
Despite the code differences in those tools, they all connect to the same infrastructure, which Kaspersky previously linked to ToddyCat, a group of Chinese cyber spies.
Update 10/12 – Shortly after publishing this report, Kaspersky posted an update on its tracking of the ToddyCat APT, highlighting new attack methods and payloads its analysts discovered recently.
Over the past year, Kaspersky observed a parallel cluster of activity from the same threat actor, different from the one seen by Check Point, with two attack variants employing legitimate VLC executables to load malware using the DLL sideloading technique.
A notable malware deployed in these attacks is ‘Ninja Agent,’ which features file management, reverse shell, process management, and more.
Other tools ToddyCat deployed in these attacks include LoFiSe (file tracker and stealer), Cobalt Strike (penetration testing suite), DropBox Uploader, and a passive UDP backdoor.
Related Articles:
This content was originally published here.




