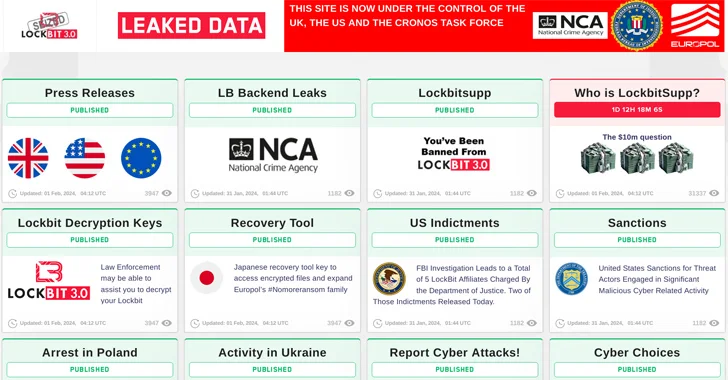
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders
The U.S. State Department has announced monetary rewards of up to $15 million for information that could lead to the identification of key leaders within the LockBit ransomware group and the arrest of any individual participating in the operation. “Since January 2020, LockBit actors have executed over 2,000 attacks against victims in the United States, […]
U.S. Offers $15 Million Bounty to Hunt Down LockBit Ransomware Leaders Read More »