New Agent Tesla Malware Variant Using ZPAQ Compression in Email Attacks
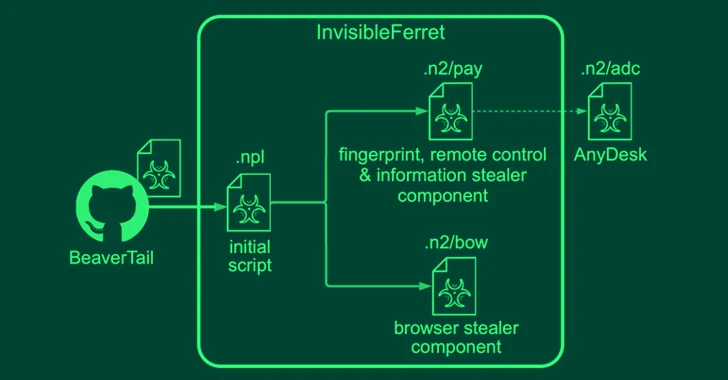
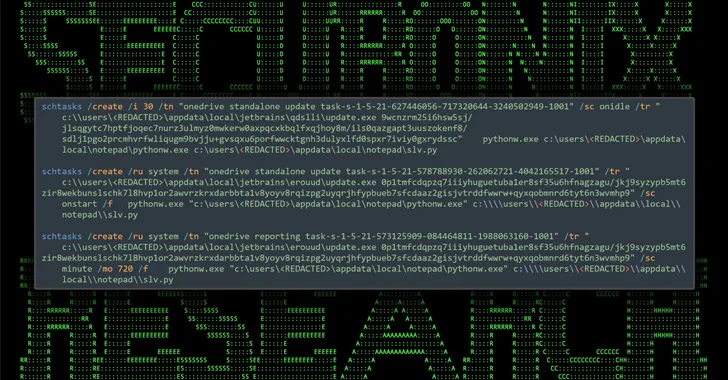
A new variant of the Agent Tesla malware has been observed delivered via a lure file with the ZPAQ compression format to harvest data from several email clients and nearly 40 web browsers. “ZPAQ is a file compression format that offers a better compression ratio and journaling function compared to widely used formats like ZIP […]
New Agent Tesla Malware Variant Using ZPAQ Compression in Email Attacks Read More »